Source: https://top-list.co/top-best-tips-for-surfing-the-web-safely-and-anonymously-v3597.html
1. Use a VPN, 2. Use the Settings on Your Browser, 3. Use an Encrypted Messaging App, 4. Update Your Cybersecurity Game, 5. Consider an Identity Theft Program, 6. Invest in a Password Manager, 7. Use TOR, 8. Use a Proxy Server, 9. Delete Cookies. Failure to take Internet security seriously might result in significant losses. It has the potential to harm you economically, socially, and personally. Smart internet usage and strategic security measures help to keep your online searches secret and prevent anyone from prying into your interests, from the government to the bored teen hacker next door, from snooping into your interests. Toplist has prepared the best tips for surfing the web safely and anonymously for you.
- Use a VPN
- Use the Settings on Your Browser
- Use an Encrypted Messaging App
- Update Your Cybersecurity Game
- Consider an Identity Theft Program
- Invest in a Password Manager
- Use TOR
- Use a Proxy Server
- Delete Cookies
Use a VPN
Using a VPN, or virtual private network server is the best and safest way to browse the internet anonymously. Because you download the proxy, so a VPN is different from a web-based proxy server because the proxy only works on your device. You still need to pick a trustworthy VPN service provider.
There are several ways a VPN keeps you anonymous online. The first is that your IP address is concealed. A VPN sends the request to one of its many safe servers while concealing your IP address by sending it through a virtual tunnel (this is why using a VPN is also known as tunneling). You can pick the server you want to use, making it impossible for anyone to identify you if they witness your online activities because they would believe you are in a different city or country.
Use a VPN
Use the Settings on Your Browser
Use Private Browsing mode if you’re on a shared or public computer by selecting this option in your browser’s options. To prevent tracking, you should also access the settings on your browser. This requests that websites not access your location data, but you’ll have to pray that they comply. Installing an anti-tracker browser plugin blocks tracking cookies so that your location stays hidden. While you’re there, make sure no Java or Adobe Flash plugins are actions that could be leaking your information to snoopers.
There are several websites with varying levels of security, and if you go to some dubious sites, your chances of experiencing a cyberattack rise. Websites, where you can download free music and movies, are especially susceptible to this. People have acquired malware from such devices in multiple cases. Always download apps from specialized app stores, such as the Apple Store or Google Play Store, as these are trusted vendors with stricter security standards.
Use the Settings on Your Browser
Use an Encrypted Messaging App
Anyone who uses the internet for communication should be really concerned about internet spying. Large tech companies have repeatedly appeared in the news for privacy infractions that leave you vulnerable to hackers, government officials, or even your bosses. Consider utilizing an encrypted messaging service to reduce the chance that third parties will be able to access your correspondence. The level of encryption varies from one to the next; with some offering modest privacy while others have advanced features like self-destructing messages.
Additionally, certain messaging apps feature end-to-end encryption, which essentially ensures that no one can access the data while it travels between your phone and the recipients. This helps prevents hackers from overhearing your talks and stealing your data, as well as preventing the government from spying. Apps for encrypted communications are more secure than telephone calls, text messages, regular emails, and even the post office because of these factors. Choose a messaging app that goes to great lengths to ensure that your discussions remain private by taking into account the level of privacy you desire and require.
Use an Encrypted Messaging App
Update Your Cybersecurity Game
Software updates are essential for them to perform much better as every software cannot be said to be perfect. It always requires updates be it changes in services, circumstances, legal compliances, glitches, or security. Updates fine-tune the software so that it operates in a safer and more legally sound environment. These are important to reduce the risk associated with it because of connectivity with the internet, and sustain the market.
The good news is that leading antivirus companies are constantly rolling out new software and technologies that stymy these new forms of cyber attacks. It’s a good idea to check in with your computer’s antivirus software regularly and, if necessary, think about switching it out for a program that’s more appropriate for the time. It’ll help you surf the web more safely without hackers stealing your information.
Update Your Cybersecurity Game
Consider an Identity Theft Program
A recent Federal Trade Commission investigation revealed some startling statistics concerning the incidence of identity theft in the United States. More than 650,000 reports of identity theft were filed in 2019, including credit card fraud, phone or utility fraud, banking fraud, and tax-related fraud. As hackers develop more advanced methods of extracting information from people, this number is unlikely to diminish in the coming years, especially given the expanding popularity of online banking, shopping, and medical services.
Identity theft protection services provide around-the-clock security that could benefit everyone who shares information online. ID theft can follow your credit card transactions, identify changes in your credit score, and track the deep web to alert you if any of your information is being sold or used for illegal purposes. ID theft is something to think about as more and more personal lives are performed online.
Consider an Identity Theft Program
Invest in a Password Manager
All passwords are encrypted and stored privately, so no one, other than the authorized user has access to their passwords. It takes care of timely password update reminders and password reset. Creating a secure password these days can feel like an advanced degree in alphanumeric. When you consider how many passwords require for different social media accounts, emails, banks, streaming platforms, subscriptions, and shopping sites, you should never use the same password twice.
There are numerous password management tools on the market. While their primary role is the same—keeping your passwords secure—password management programs can provide much more in terms of data security. Consult with an MSP who specializes in cybersecurity to assist you to choose the best password management product for your company. But, remember, there is no alternative for proper password hygiene, so no matter what tool you use, you must still adhere to basic cybersecurity standards.
Invest in a Password Manager
Use TOR
Using a TOR browser is one of the safest ways to browse the internet anonymously. This route your internet traffic through a deeply nested set of TOR servers, so that anyone attempting to link your internet activity to your personal information will only see the IP address of the final node. TOR browsing is extremely safe, which is why it is frequently connected with the dark web, which houses illegal websites. The disadvantage of using the TOR is that it would most certainly significantly slow down your browsing speed.
Tor Browser is used to access the entire internet, including the dark web. Because of its various layers, it is also known as Tor Browser or The Onion Router. Because Tor is built on Firefox, you can still access popular sites from the surface web, such as YouTube and Wikipedia. Tor encrypts your traffic and routes it through stopping points (nodes) before arriving at its final destination – the website you visit. Any Tor user can offer to use their network as a node. Your traffic passes via three tiers of nodes: an entry, a relay, and an exit.
Use TOR
Use a Proxy Server
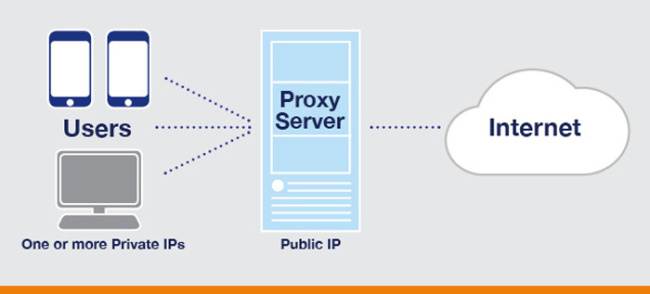
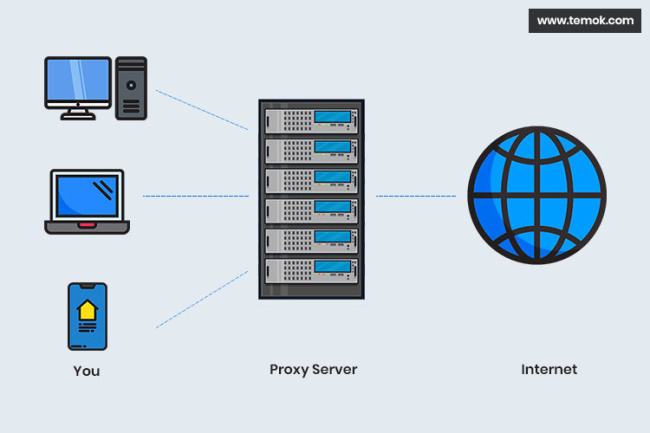
There are numerous proxy servers available that allow you to browse the internet anonymously and frequently for free. You don’t need to download anything if you utilize a web-based proxy server. You simply go to the web proxy site and type in the URL of the site you wish to see. Essentially, the proxy site retrieves data from the website you wish to access and provides it to you so that anyone attempting to trace your activity sees the proxy site’s IP address rather than your own.
If using a proxy server, client computers will first connect to the proxy server, requesting some resources like web pages, games, videos, mp3, e-books, or any other resources which are available from various servers over the Internet. Proxy sites are easy to use and usually free, but they are not always effective. Many websites identify and prevent access to web-based proxy servers. There’s also the risk of being duped by a honeypot site that masquerades as a secure proxy server but actually steals your data.
Use a Proxy Server
Delete Cookies
When you use a web browser, cookies are stored on your computer. The server on the other end of the connection reads the cookie file. Most of the time, cookies are a beneficial thing—without authentication cookies, you’d have to enter usernames and passwords every time you visited a website, on every page. Cookies also allow online shopping carts to function without losing all of your items prior to purchasing.
Cookies are generally beneficial, but they can also monitor you. Control a little portion of your online privacy by blocking, removing, and allowing only specific cookies. You should also configure your browser to remove all cookies at the conclusion of each session so that anyone who uses the computer after you does not find your personal information via autofill. Deleting cookies also prevents websites from displaying those obnoxious tracking adverts.
Delete Cookies